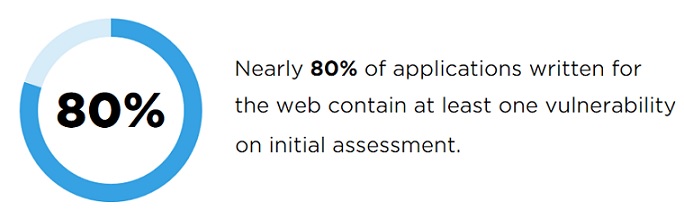
There once was a time in software development where developers could design, build and then think about their software's security. However in today's highly connected, API-driven application environment, this approach is simply too risky as it exposes the software to vulnerabilities ...
DevSecOps
For the past 13 years, the Ponemon Institute has examined the cost associated with data breaches of less than 100,000 records, finding that the costs have steadily risen over the course of the study. The average cost of a data breach was $3.86 million in the 2018 study, compared to $3.50 million in 2014 – representing nearly 10 percent net increase over the past 5 years of the study ...
Hidden costs in data breaches – such as lost business, negative impact on reputation and employee time spent on recovery – are difficult and expensive to manage, according to the 2018 Cost of a Data Breach Study, sponsored by IBM Security and conducted by Ponemon Institute. The study found that the average cost of a data breach globally is $3.86 million ...
The previous chapter in this WhiteHat Security series discussed dependencies as the second step of the Twelve-Factor App. This next chapter examines the security component of step three of the Twelve-Factor methodology — storing configurations within the environment.
Even organizations that understand the importance of cybersecurity in theory often stumble when it comes to marrying security initiatives with their development and operations processes. Most businesses agree that everyone should be responsible for security, but this principle is not being upheld on a day-to-day basis in many organizations. That’s bad news for everyone. Here are some best practices for implementing SecOps ...
While the technologies, processes, and cultural shifts of DevOps have improved the ability of software teams to deliver reliable work rapidly and effectively, security has not been a focal point in the transformation of cloud IT infrastructure. SecOps is a methodology that seeks to address this by operationalizing and hardening security throughout the software lifecycle ...
Despite 95 percent of CIOs expecting cyberthreats to increase over the next three years, only 65 percent of their organizations currently have a cybersecurity expert, according to a survey from Gartner. The survey also reveals that skills challenges continue to plague organizations that undergo digitalization, with digital security staffing shortages considered a top inhibitor to innovation ...
In the shift to cloud native, many organizations have adopted a configuration-as-code approach. This helps drive up application deployment velocity by letting developers and DevOps teams reconfigure their deployments as their needs arise. Other organizations, particularly the more regulated ones, still have security people owning these tools, but that creates increased pressure on the security organization to keep up. How much are organizations investing in this process, and how much is it getting them? ...
More than a third of companies that use serverless functions are not employing any application security best practices and are not using any tools or standard security methodologies to secure them, according to the State of Serverless Security survey, conducted by PureSec ...
The previous chapter in this WhiteHat Security series discussed Codebase as the first step of the Twelve-Factor App and defined a security best practice approach for ensuring a secure source control system. Considering the importance of applying security in a modern DevOps world, this next chapter examines the security component of step two of the Twelve-Factor methodology. Here follows some actionable advice from the WhiteHat Security Addendum Checklist, which developers and ops engineers can follow during the SaaS build and operations stages ...
An overwhelming 83 percent of respondents have concerns about deploying traditional firewalls in the cloud, according to Firewalls and the Cloud, a survey conducted by Barracuda Networks...
The Twelve-Factor App is a methodology that offers a 12-step best practice approach for developers to apply when building software-as-a-service apps that are both scalable and maintainable in a DevOps world. As software continues to be written and deployed at a faster rate and in the cloud, development teams are finding there is more room for failure and vulnerabilities. This blog series will discuss how to build a Twelve-Factor app securely ...
DevOps and security traditionally have been siloed functions and security is often seen as a policing function by DevOps team members. However, more mature business leaders are trying to bridge the gap between the two functions to achieve business excellence. This theme was evident from our recent survey where 39% of respondents cited that DevOps and development teams care greatly about their cybersecurity posture, showing that the silo between security/IT and development teams is diminishing ...
DEVOPSdigest asked experts from across the IT industry for their opinions on the top tools to support DevSecOps. Part 5, the last installment, offers some final thoughts about "tools" that are not necessarily technology ...
DEVOPSdigest asked experts from across the IT industry for their opinions on the top tools to support DevSecOps. Part 4 covers code and data ...
DEVOPSdigest asked experts from across the IT industry for their opinions on the top tools to support DevSecOps. Part 3 covers security and monitoring ...
DEVOPSdigest asked experts from across the IT industry for their opinions on the top tools to support DevSecOps. Part 2 covers DevOps and development ...
While DevSecOps, much like DevOps itself, is more about changing IT culture than employing certain types of technology, some tools can be an important support. To find out what the right tools are, DEVOPSdigest asked experts from across the IT industry for their opinions on the top tools to support DevSecOps. Part 1 covers the testing phase ...
With data breaches consistently being in the news over the last several years, it is no wonder why data privacy has become such a hot topic and why the European Union (EU) has put in place General Data Protection Regulation (GDPR) which will become enforceable on May 25, 2018, which is less than a month away ...
When it comes to operations and development, DevOps has changed the traditional compartmentalized style of development by eliminating silos. But what about the security team? Security is largely still siloed from operations and development. No doubt, many DevOps teams have some security controls baked into their automation processes, but a recent survey shows there are still alarming gaps ...
According to the 2018 Global Security Trends in the Cloud report, 93 percent of respondents faced challenges when deploying their current on-premises security tools in the cloud, and 97 percent lacked the tools, cross-functional collaboration and resources to gain proper insight into security across the organization. These numbers indicate a big problem in DevSecOps that needs to be addressed ...
Only 52 percent of developers using commercial or open source components in their applications update those components when a new security vulnerability is announced, according to new research conducted by Vanson Bourne for CA Veracode, part of CA Technologies. This highlights organizations' lack of security awareness and puts organizations at risk of a breach ...
A recent CEB, now Gartner, survey found that nearly 20 percent of organizations observed at least one IoT-based attack in the past three years. To protect against those threats Gartner, forecasts that worldwide spending on IoT security will reach $1.5 billion in 2018, a 28 percent increase from 2017 spending of $1.2 billion.
Government IT professionals surveyed, as part of F5 Networks' State of Application Delivery report, made it clear they are heavily focused on building the foundation necessary for application-driven digital transformation. Around the world, government organizations are shifting towards digital government, and with that we see government organizations embracing the cloud, adopting automation and orchestration, and adjusting security strategies ...